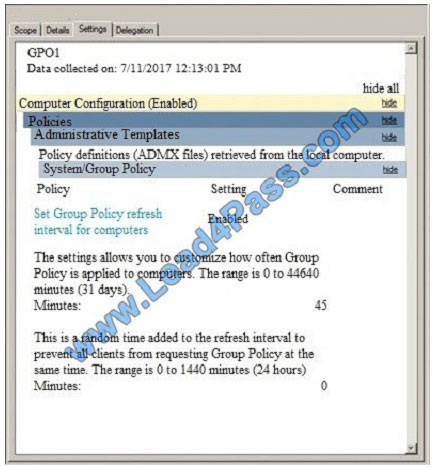
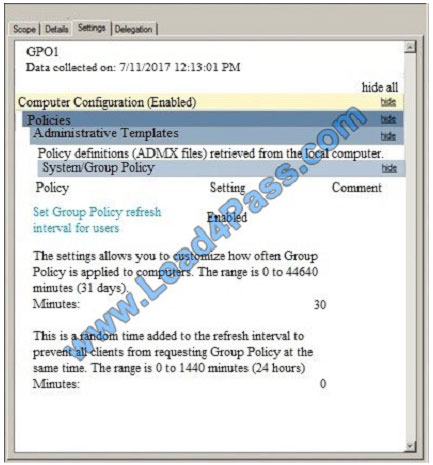
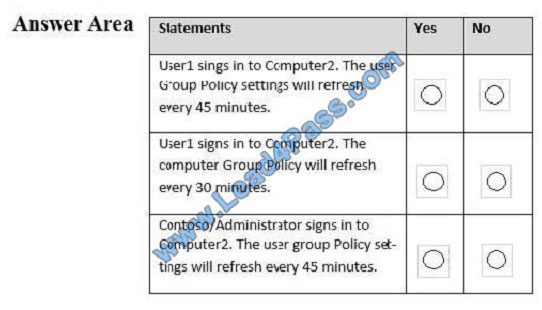
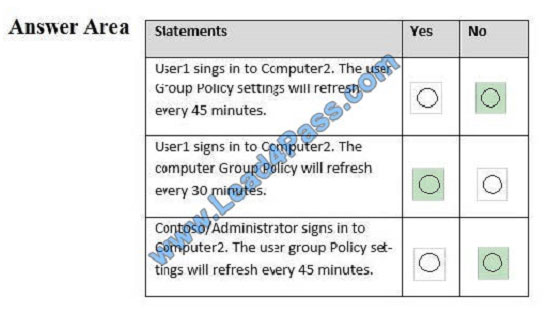
The best and most updated latest CompTIA Security+ JK0-018 dumps exam practice materials in PDF format download free try from lead4pass. “CompTIA Security+ E2C (2011 Edition)” is the name of CompTIA Security+ https://www.leads4pass.com/jk0-018.html exam dumps which covers all the knowledge points of the real CompTIA exam.
High quality CompTIA Security+ JK0-018 dumps pdf training resources update free shared. Practice for your CompTIA JK0-018 exam with the help of lead4pass. You can download CompTIA Security+ JK0-018 dumps pdf training material from lead4pass and pass the CompTIA JK0-018 exam test easily in the first attempt.
Latest CompTIA JK0-018 dumps pdf free download from google drive: https://drive.google.com/open?id=1pJKQBZf35TH3QSBqQqsIS9bAMjkoKvfG
Latest CompTIA JK0-016 dumps pdf free download from google drive: https://drive.google.com/open?id=0B_7qiYkH83VRdGRfblRva2lwQjg
New CompTIA Security+ JK0-018 Dumps Exam Questions And Answers (Q1-Q40)
QUESTION 1
Which of the following application security testing techniques is implemented when an automated system generates random input data?
A. Fuzzing
B. XSRF
C. Hardening
D. Input validation
Correct Answer: A
QUESTION 2
Which of the following can be used by a security administrator to successfully recover a user’s forgotten password on a password protected file?
A. Cognitive password
B. Password sniffing
C. Brute force
D. Social engineering
Correct Answer: C
QUESTION 3
A security administrator wants to check user password complexity. Which of the following is the BEST tool to use?
A. Password history
B. Password logging
C. Password cracker
D. Password hashing
Correct Answer: C
QUESTION 4
Certificates are used for: (Select TWO).
A. Client authentication.
B. WEP encryption.
C. Access control lists.
D. Code signing.
E. Password hashing.
Correct Answer: AD
QUESTION 5
Which of the following is a hardware based encryption device?
A. EFS
B. TrueCrypt
C. TPM
D. SLE
Correct Answer: C
QUESTION 6
Which of the following BEST describes a protective countermeasure for SQL injection?
A. Eliminating cross-site scripting vulnerabilities
B. Installing an IDS to monitor network traffic
C. Validating user input in web applications
D. Placing a firewall between the Internet and database servers
Correct Answer: C
QUESTION 7
JK0-018 dumps Which of the following MOST interferes with network-based detection techniques?
A. Mime-encoding
B. SSL
C. FTP
D. Anonymous email accounts
Correct Answer: B
QUESTION 8
A certificate authority takes which of the following actions in PKI?
A. Signs and verifies all infrastructure messages
B. Issues and signs all private keys
C. Publishes key escrow lists to CRLs
D. Issues and signs all root certificates
Correct Answer: D
QUESTION 9
Use of a smart card to authenticate remote servers remains MOST susceptible to which of the following attacks?
A. Malicious code on the local system
B. Shoulder surfing
C. Brute force certificate cracking
D. Distributed dictionary attacks
Correct Answer: A
QUESTION 10
Separation of duties is often implemented between developers and administrators in order to separate which of the following?
A. More experienced employees from less experienced employees
B. Changes to program code and the ability to deploy to production
C. Upper level management users from standard development employees
D. The network access layer from the application access layer
Correct Answer: B
QUESTION 11
A security administrator needs to update the OS on all the switches in the company. Which of the following MUST be done before any actual switch configuration is performed?
A. The request needs to be sent to the incident management team.
B. The request needs to be approved through the incident management process.
C. The request needs to be approved through the change management process.
D. The request needs to be sent to the change management team.
Correct Answer: C
QUESTION 12
Jane, an individual, has recently been calling various financial offices pretending to be another person to gain financial information. Which of the following attacks is being described?
A. Phishing
B. Tailgating
C. Pharming
D. Vishing
Correct Answer: D
QUESTION 13
A user in the company is in charge of various financial roles but needs to prepare for an upcoming audit. They use the same account to access each financial system. Which of the following security controls will MOST likely be implementedwithin the company?
A. Account lockout policy
B. Account password enforcement
C. Password complexity enabled
D. Separation of duties
Correct Answer: D
QUESTION 14
A CRL is comprised oF.
A. Malicious IP addresses.
B. Trusted CA’s.
C. Untrusted private keys.
D. Public keys.
Correct Answer: D
QUESTION 15
Sara, a user, downloads a keygen to install pirated software. After running the keygen, system performance is extremely slow and numerous antivirus alerts are displayed. JK0-018 dumps Which of the following BEST describes this type of malware?
A. Logic bomb
B. Worm
C. Trojan
D. Adware
Correct Answer: C
QUESTION 16
Which of the following may significantly reduce data loss if multiple drives fail at the same time?
A. Virtualization
B. RAID
C. Load balancing
D. Server clustering
Correct Answer: B
QUESTION 17
Which of the following should be considered to mitigate data theft when using CAT5 wiring?
A. CCTV
B. Environmental monitoring
C. Multimode fiber
D. EMI shielding
Correct Answer: D
QUESTION 18
To help prevent unauthorized access to PCs, a security administrator implements screen savers that lock the PC after five minutes of inactivity. Which of the following controls is being described in this situation?
A. Management
B. Administrative
C. Technical
D. Operational
Correct Answer: C
QUESTION 19
Pete, a network administrator, is capturing packets on the network and notices that a large amount of the traffic on the LAN is SIP and RTP protocols. Which of the following should he do to segment that traffic from the other traffic?
A. Connect the WAP to a different switch.
B. Create a voice VLAN.
C. Create a DMZ.
D. Set the switch ports to 802.1q mode.
Correct Answer: B
QUESTION 20
Which of the following IP addresses would be hosts on the same subnet given the subnet mask 255.255.255.224? (Select TWO).
A. 10.4.4.125
B. 10.4.4.158
C. 10.4.4.165
D. 10.4.4.189
E. 10.4.4.199
Correct Answer: CD
QUESTION 21
Which of the following algorithms has well documented collisions? (Select TWO).
A. AES
B. MD5
C. SHA
D. SHA-256
E. RSA
Correct Answer: BC
QUESTION 22
Which of the following is BEST used as a secure replacement for TELNET?
A. HTTPS
B. HMAC
C. GPG
D. SSH
Correct Answer: D
QUESTION 23
An email client says a digital signature is invalid and the sender cannot be verified. The recipient is concerned with which of the following concepts?
A. Integrity
B. Availability
C. Confidentiality
D. Remediation
Correct Answer: A
QUESTION 24
Which of the following is an effective way to ensure the BEST temperature for all equipment within a datacenter?
A. Fire suppression
B. Raised floor implementation
C. EMI shielding
D. Hot or cool aisle containment
Correct Answer: D
QUESTION 25
Which of the following transportation encryption protocols should be used to ensure maximum security between a web browser and a web server? JK0-018 dumps
A. SSLv2
B. SSHv1
C. RSA
D. TLS
Correct Answer: D
QUESTION 26
Developers currently have access to update production servers without going through an approval process. Which of the following strategies would BEST mitigate this risk?
A. Incident management
B. Clean desk policy
C. Routine audits
D. Change management
Correct Answer: D
QUESTION 27
Which of the following is a difference between TFTP and FTP?
A. TFTP is slower than FTP.
B. TFTP is more secure than FTP.
C. TFTP utilizes TCP and FTP uses UDP.
D. TFTP utilizes UDP and FTP uses TCP.
Correct Answer: D
QUESTION 28
Matt, an administrator, notices a flood fragmented packet and retransmits from an email server. After disabling the TCP offload setting on the NIC, Matt sees normal traffic with packets flowing in sequence again.
Which of the following utilities was he MOST likely using to view this issue?
A. Spam filter
B. Protocol analyzer
C. Web application firewall
D. Load balancer
Correct Answer: B
QUESTION 29
Which of the following is characterized by an attacker attempting to map out an organization’s staff hierarchy in order to send targeted emails?
A. Whaling
B. Impersonation
C. Privilege escalation
D. Spear phishing
Correct Answer: A
QUESTION 30
Which of the following would a security administrator implement in order to discover comprehensive security threats on a network?
A. Design reviews
B. Baseline reporting
C. Vulnerability scan
D. Code review
Correct Answer: C
QUESTION 31
Which of the following is an example of a false positive?
A. Anti-virus identifies a benign application as malware.
B. A biometric iris scanner rejects an authorized user wearing a new contact lens.
C. A user account is locked out after the user mistypes the password too many times.
D. The IDS does not identify a buffer overflow.
Correct Answer: A
QUESTION 32
Data execution prevention is a feature in most operating systems intended to protect against which type of attack?
A. Cross-site scripting
B. Buffer overflow
C. Header manipulation
D. SQL injection
Correct Answer: B
QUESTION 33
Use of group accounts should be minimized to ensure which of the following?
A. Password security
B. Regular auditing
C. Baseline management
D. Individual accountability
Correct Answer: D
QUESTION 34
Privilege creep among long-term employees can be mitigated by which of the following procedures?
A. User permission reviews
B. Mandatory vacations
C. Separation of duties
D. Job function rotation
Correct Answer: A
QUESTION 35
In which of the following scenarios is PKI LEAST hardened?
A. The CRL is posted to a publicly accessible location.
B. The recorded time offsets are developed with symmetric keys.
C. A malicious CA certificate is loaded on all the clients.
D. All public keys are accessed by an unauthorized user.
Correct Answer: C
QUESTION 36
Configuring the mode, encryption methods, and security associations are part of which of the following?
A. IPSec
B. Full disk encryption
C. 802.1x
D. PKI
Correct Answer: A
QUESTION 37
Which of the following assessments would Pete, the security administrator, use to actively test that an application’s security controls are in place?
A. Code review
B. Penetration test
C. Protocol analyzer
D. Vulnerability scan
Correct Answer: B
QUESTION 38
A security administrator has just finished creating a hot site for the company. JK0-018 dumps This implementation relates to which of the following concepts?
A. Confidentiality
B. Availability
C. Succession planning
D. Integrity
Correct Answer: B
QUESTION 39
In the initial stages of an incident response, Matt, the security administrator, was provided the hard drives in question from the incident manager. Which of the following incident response procedures would he need to perform in order to begin
the analysis? (Select TWO).
A. Take hashes
B. Begin the chain of custody paperwork
C. Take screen shots
D. Capture the system image
E. Decompile suspicious files
Correct Answer: AD
QUESTION 40
Which of the following is used to certify intermediate authorities in a large PKI deployment?
A. Root CA
B. Recovery agent
C. Root user
D. Key escrow
Correct Answer: A
Why Choose Lead4pass?
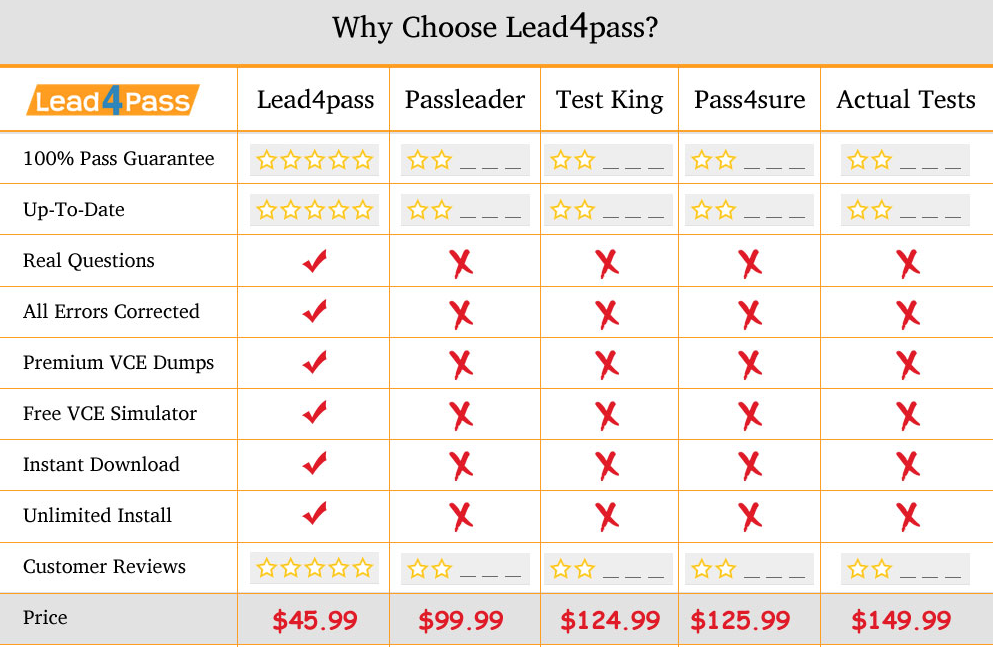
High quality IT learning materials offered by the best provider lead4pass. From the following picture, you can see there is a difference between lead4pass and other brands. Other brands started earlier, but the questions are not the latest and it is very expensive. Lead4pass provide the cheapest and newest questions with high pass rate, help you pass CompTIA JK0-018 exam easily.
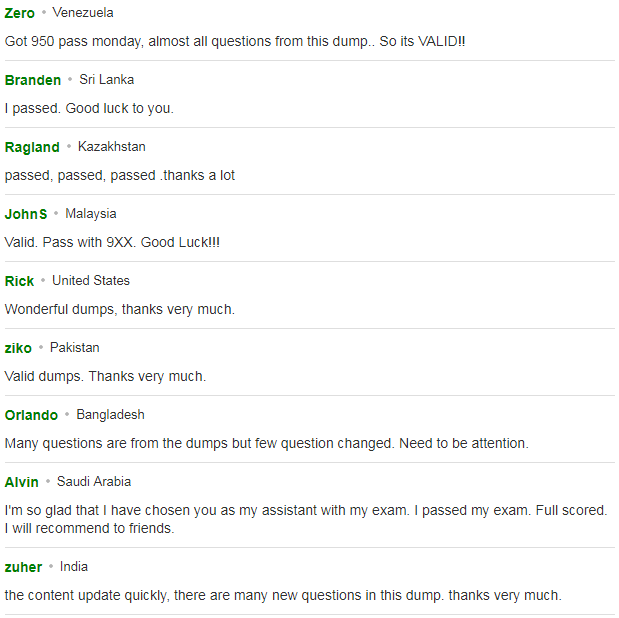
What Our Customers Are Saying:
Click here to have a review about us: https://www.resellerratings.com/store/lead4pass
Useful CompTIA Security+ JK0-018 dumps exam questions and answers update free try. Helpful newest CompTIA Security+ https://www.leads4pass.com/jk0-018.html dumps pdf training resources which are the best for clearing JK0-018 exam test, and to get certified by CompTIA Security+. Download CompTIA Security+ JK0-018 dumps exam questions and verified answers. It is the best choice for you to pass CompTIA JK0-018 exam easily.