[High Quality Exam Dumps] Right Choice for Microsoft 70-534 Dumps Exam Free Youtube Demo
Why choose lead4pass Microsoft 70-534 dumps exam? It is the right choice for Microsoft 70-534 dumps exam. Lead4pass offers best Microsoft Specialist: Microsoft Azure 70-534 dumps exam training resources in PDF format free download. Useful Microsoft Specialist: Microsoft Azure 70-534 dumps pdf files and vce youtube demo update free shared. “Architecting Microsoft Azure Solutions” is the name of Microsoft Specialist: Microsoft Azure https://www.leads4pass.com/70-534.html exam dumps which covers all the knowledge points of the real Microsoft Specialist: Microsoft Azure. Latest Microsoft Specialist: Microsoft Azure 70-534 dumps exam practice questions and answers update free try, pass Microsoft 70-534 exam test quickly and easily at first attempt.
High quality Microsoft 70-534 dumps pdf files: https://drive.google.com/open?id=0B_7qiYkH83VRX0JJVFo2eEctTW8
High quality Microsoft 70-533 dumps pdf files: https://drive.google.com/open?id=0B_7qiYkH83VRZF9feEh5eDcwVzA

Best Microsoft Specialist: Microsoft Azure 70-534 dumps exam questions and answer (1-15)
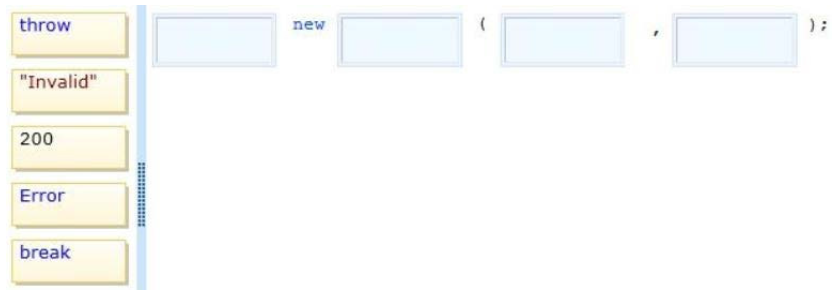
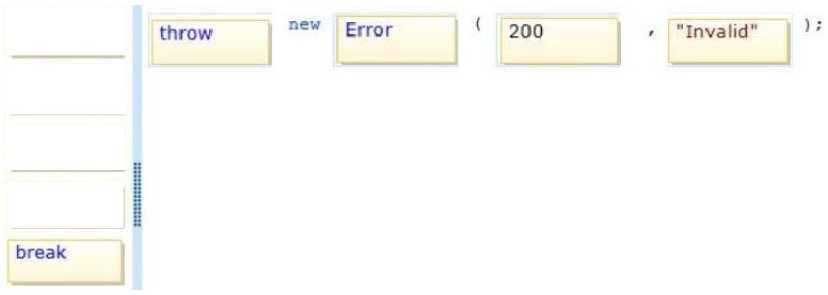
QUESTION 1
You need to assign permissions for the Virtual Machine workloads that you migrate to Azure.
The solution must use the principal of least privileges.
What should you do?
A. Create all VMs in the cloud service named Groupl and then connect to the Azure subscription.
Run the following Windows PowerShell command:
New-AzureRoleAssignment -Mail [email protected] -RoleDefinitionName Contributor – ResoureeGroupName group1
B. In the Azure portal, select an individual virtual machine and add an owner.
C. In the Azure portal, assign read permission to the user at the subscription level.
D. Create each VM in a separate cloud service and then connect to the Azure subscription. Run the following Windows PowerShell command:
Get-AzureVM | New-AzureRoleAssignment -Mail [email protected] -RoleDefinitionName Contributor
Correct Answer: A
QUESTION 2
You need to design the system that alerts project managers to data changes in the contractor information app.
Which service should you use?
A. Azure Mobile Service
B. Azure Service Bus Message Queueing
C. Azure Queue Messaging
D. Azure Notification Hub
Correct Answer: B
QUESTION 3
You need to recommend a solution that allows partners to authenticate.
Which solution should you recommend?
A. Configure the federation provider to trust social identity providers.
B. Configure the federation provider to use the Azure Access Control service.
C. Create a new directory in Azure Active Directory and create a user account for the partner.
D. Create an account on the VanArsdel domain for the partner and send an email message that contains the password to the partner.
Correct Answer: B
QUESTION 4
You are designing a plan to deploy a new application to Azure. The solution must provide a single sign-on experience for users. 70-534 dumps
You need to recommend an authentication type.
Which authentication type should you recommend?
A. SAML credential tokens
B. Azure managed access keys
C. Windows Authentication
D. MS-CHAP
Correct Answer: A
QUESTION 5
You need to prepare the implementation of data storage for the contractor information app.
What should you?
A. Create a storage account and implement multiple data partitions.
B. Create a Cloud Service and a Mobile Service. Implement Entity Group transactions.
C. Create a Cloud Service and a Deployment group. Implement Entity Group transactions.
D. Create a Deployment group and a Mobile Service. Implement multiple data partitions.
Correct Answer: B
Explanation:
/ VanArsdel needs a solution to reduce the number of operations on the contractor information table.
Currently, data transfer rates are excessive, and queue length for read/write operations affects performance.
QUESTION 6
You need to ensure that users do not need to re-enter their passwords after they authenticate to cloud applications for the first time.
What should you do?
A. Enable Microsoft Account authentication.
B. Set up a virtual private network (VPN) connection between the VanArsdel premises and Azure datacenter. Set up a Windows Active Directory domain controller in Azure VM. Implement Integrated Windows authentication.
C. Deploy ExpressRoute.
D. Configure Azure Active Directory Sync to use single sign-on (SSO).
Correct Answer: D
QUESTION 7
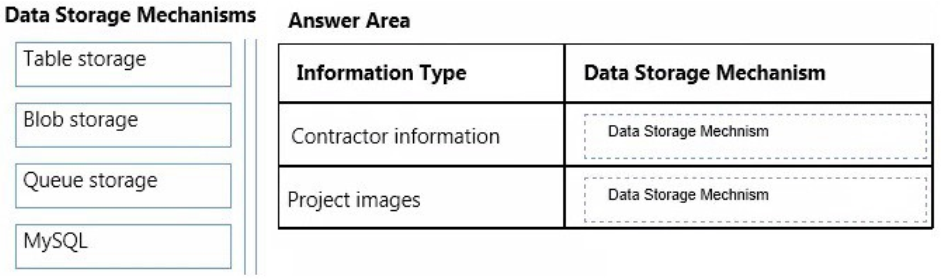
You need to recommend data storage mechanisms for the solution.
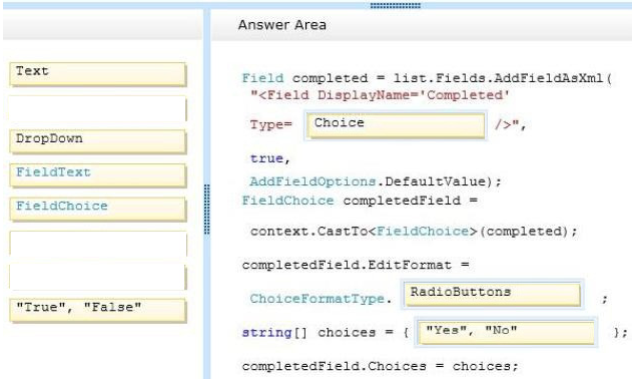
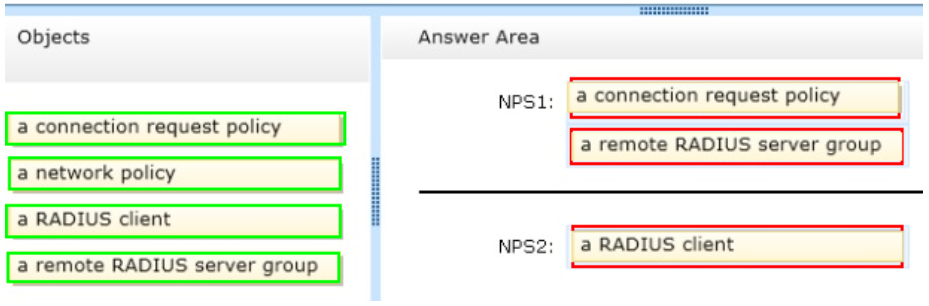
What should you recommend? To answer, drag the appropriate data storage mechanism to the correct information type. Each data storage mechanism may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:
Correct Answer:
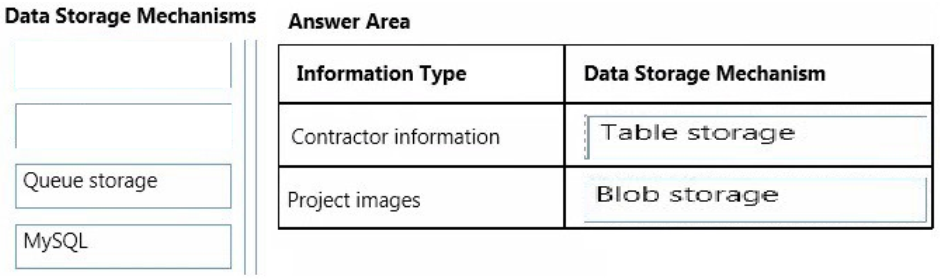
QUESTION 8
You need to confgure the deployment of the storage analysis applicaton.
What should you do?
A. Create a new Mobile Service.
B. Confgure the deployment from source control.
C. Add a new deployment slot.
D. Turn on contnuous integraton.
Correct Answer: B
QUESTION 9
You are planning an upgrade strategy for an existing Azure application. Multiple instances of the application run in Azure. The management team is concerned about application downtime due to a business service level agreement (SLA).
You are evaluating which change in your environment will require downtime. You need to identify the changes to the environment that will force downtime.
Which change always requires downtime?
A. Adding an HTTPS endpoint to a web role
B. Upgrading the hosted service by deploying a new package
C. Changing the value of a configuration setting
D. Changing the virtual machine size
Correct Answer: A
QUESTION 10
An application currently resides on an on-premises virtual machine that has 2 CPU cores 4 GB of RAM 20 GB of hard disk space and a 10 megabit/second network connection. 70-534 dumps
You plan to migrate the application to Azure. You have the following requirements:
You must not make changes to the application.
You must minimize the costs for hosting the application.
You need to recommend the appropriate virtual machine instance type.
Which virtual machine tier should you recommend?
A. Network Optimized (A Series)
B. General Purpose Compute Basic Tier (A Series)
C. General Purpose Compute Standard Tier (A Series)
D. Optimized Compute (D Series)
Correct Answer: B
QUESTION 11
You are designing an Azure development environment. Team members learn Azure development techniques by training in the development environment.
The development environment must auto scale and load balance additional virtual machine (VM) instances. You need to recommend the most cost-effective compute-instance size that allows team members to work with Azure in the development environment.
What should you recommend?
A. Azure Al standardVM Instance
B. Azure A2 basic VM Instance
C. Azure A3 basic VM Instance
D. Azure A9 standard VM Instance
Correct Answer: A
QUESTION 12
You are designing an Azure application. The application includes services hosted in different geographic locations. The service locations may change.
You must minimize the cost of communication between services.
You need to recommend an approach for data transmission between your application and Azure services.
The solution must minimize administrative effort.
What should you recommend?
A. Azure Table storage
B. Service Bus
C. Service Management API
D. Azure Queue storage
Correct Answer: B
QUESTION 13
You are running a Linux guest in Azure Infrastructure-as-a-Service (IaaS). You must run a daily maintenance task. The maintenance task requires native BASH commands.
You need to configure Azure Automation to perform this task.
Which three actions should you perform? Each correct answer presents part of the solution.
A. Create an automation account.
B. Create an Orchestrator runbook.
C. Create an asset credential.
D. Run the Invoke-Workflow Azure PowerShell cmdlet.
E. Import the SSH PowerShell Module.
Correct Answer: ACE
QUESTION 14
You are designing an Azure web application.
All users must authenticate by using Active Directory Domain Services (AD DS) credentials. You need to recommend an approach to enable single sign-on to the application for domain-authenticated users. Which two actions should you recommend? Each correct answer presents part of the solution.
A. Use Forms authentication to generate claims.
B. Use the SQL membership provider in the web application.
C. Use Windows Identity Foundation in the web application.
D. Use Active Directory Federation Services (AD FS) to generate claims.
Correct Answer: C
QUESTION 15
You are designing an Azure application that will use a worker role. The worker role will create temporary files.
You need to minimize storage transaction charges. 70-534 dumps
Where should you create the files?
A. In Azure local storage
B. In Azure Storage page blobs
C. On an Azure Drive
D. In Azure Storage block blobs
Correct Answer: A
Here are some reviews from our customers:
Click here to have a review about us: https://www.resellerratings.com/store/lead4pass
Newest Microsoft Specialist: Microsoft Azure 70-534 dumps pdf practice materials and study guides free download from lead4pass. The best and most updated latest Microsoft Specialist: Microsoft Azure https://www.leads4pass.com/70-534.html dumps pdf training resources which are the best for clearing 70-534 exam test, and to get certified by Microsoft Microsoft Specialist: Microsoft Azure, free download with high pass guarantee.
Latest Microsoft Specialist: Microsoft Azure 70-534 dumps vce youtube: https://youtu.be/yN_VWCJcXgo
Why Lead 4 pass?
Lead4pass is the best IT learning material provider. Other brands appeared early, the questions are not the latest and it is vert expensive. Lead4pass provide the newest and cheapest questions and answers. Lead 4 pass is the correct choice for IT learning materials, help you pass your exam easily.


 The page must be rendered so that the <div>tag is not forced to be separate from the other content. 70-480 dumps The following graphic shows the correctly rendered output.
The page must be rendered so that the <div>tag is not forced to be separate from the other content. 70-480 dumps The following graphic shows the correctly rendered output.